13 jan 2017

The Israeli occupation authorities released on Friday Abdulsalam Abu Ghazaleh, father of the martyr Thaer Abu Ghazaleh, after he was accused of "incitement", but ordered his expulsion from occupied Jerusalem.
According to Jumana, Abdulsalam’s sister, the Magistrate Court issued a release order on Friday providing that her brother Abu Ghazaleh gets expelled from the Old City for two weeks, and by this decision, he is also deprived of staying at his parents' home there, according to al-Quds Press news agency.
She pointed out that the Israeli occupation police arrested her brother last Tuesday after he was summoned for investigation in al-Qishleh police station to the west of occupied Jerusalem, and extended his detention twice on charges of "incitement" on Facebook.
Israeli intelligence agents raided the house of Abu Ghazaleh's family last Tuesday in the Old City of Jerusalem, tampered with its contents, confiscated electronic devices and mobile phones, and tore up pictures of martyr Abu Ghazaleh and pictures of other martyrs that were hung in the house.
Thaer Abu Ghazaleh was killed on 8th October 2015 after he carried out a stabbing attack against four Israelis in Tel Aviv. His body remained withheld in Israeli morgues until 30th August 2016.
According to Jumana, Abdulsalam’s sister, the Magistrate Court issued a release order on Friday providing that her brother Abu Ghazaleh gets expelled from the Old City for two weeks, and by this decision, he is also deprived of staying at his parents' home there, according to al-Quds Press news agency.
She pointed out that the Israeli occupation police arrested her brother last Tuesday after he was summoned for investigation in al-Qishleh police station to the west of occupied Jerusalem, and extended his detention twice on charges of "incitement" on Facebook.
Israeli intelligence agents raided the house of Abu Ghazaleh's family last Tuesday in the Old City of Jerusalem, tampered with its contents, confiscated electronic devices and mobile phones, and tore up pictures of martyr Abu Ghazaleh and pictures of other martyrs that were hung in the house.
Thaer Abu Ghazaleh was killed on 8th October 2015 after he carried out a stabbing attack against four Israelis in Tel Aviv. His body remained withheld in Israeli morgues until 30th August 2016.

Hamas hackers continue to trick Israeli soldiers into revealing sensitive military information by penetrating data stored on their smart phones.
Israeli news outlets said the Israeli occupation army unraveled 15 fake Hamas accounts on social media networks used to entrap soldiers.
The Israeli occupation army and Shin Bet have conducted a so-called “Operation Hunter’s Network” campaign to chase down Hamas network after officials received reports about a new campaign from Gaza.
In the campaign, Hamas hackers posted seductive pictures of young Israeli women on social media to attract Israeli soldiers and retrieve data from their smart phones.
An Israeli official said Hamas hackers obtained access to data by penetrating soldiers’ accounts then chatting directly with the soldier. Shortly afterwards, the account holder asks the soldier to download applications infected with Trojan Horse viruses.
After the virus reaches its destination, the Hamas operative immediately obtains access to the data on the soldiers’ phones such as pictures, text messages, conversations.
The virus also enabled Hamas operatives to access the camera and microphone, through which they could capture images and record communications. As a precautionary measure, the Israeli occupation army slapped restrictions on the use of social media by Israeli soldiers, mainly high-ranked military staff.
Israeli news outlets said the Israeli occupation army unraveled 15 fake Hamas accounts on social media networks used to entrap soldiers.
The Israeli occupation army and Shin Bet have conducted a so-called “Operation Hunter’s Network” campaign to chase down Hamas network after officials received reports about a new campaign from Gaza.
In the campaign, Hamas hackers posted seductive pictures of young Israeli women on social media to attract Israeli soldiers and retrieve data from their smart phones.
An Israeli official said Hamas hackers obtained access to data by penetrating soldiers’ accounts then chatting directly with the soldier. Shortly afterwards, the account holder asks the soldier to download applications infected with Trojan Horse viruses.
After the virus reaches its destination, the Hamas operative immediately obtains access to the data on the soldiers’ phones such as pictures, text messages, conversations.
The virus also enabled Hamas operatives to access the camera and microphone, through which they could capture images and record communications. As a precautionary measure, the Israeli occupation army slapped restrictions on the use of social media by Israeli soldiers, mainly high-ranked military staff.

The Israeli magistrate court in Beersheba on Thursday extended the detention of a Palestinian Bedouin resident of the Negev city of Rahat after he was accused of publishing a video of the latest Jerusalem vehicle-ramming attack on the Internet.
The court extended the detention of the young man, in his 30s, for five days in response to a request submitted by a public prosecution official.
The prosecutor claimed Israeli investigators needed more time to interrogate the young man after he publicized video footage of the recent ramming attack in Jerusalem, which killed four soldiers and injured about 15 others.
The court extended the detention of the young man, in his 30s, for five days in response to a request submitted by a public prosecution official.
The prosecutor claimed Israeli investigators needed more time to interrogate the young man after he publicized video footage of the recent ramming attack in Jerusalem, which killed four soldiers and injured about 15 others.
12 jan 2017

The smartphones of dozens of Israeli soldiers and officers were hacked by Hamas operatives pretending to be attractive young people online, Israeli military officials said on Wednesday.
Using fake profiles on social media with alluring photos, members of Hamas managed to network with soldiers and officers, luring them into long chats, Arabic-language spokesman for the Israeli army Avichay Adraee said in a Facebook post.
"Following reports from soldiers of suspicious activity of accounts on social media an operation was launched lasting several months led by the military intelligence aimed at uncovering enemy accounts," Adraee added
"During the operation, we uncovered dozens of accounts working to leak and steal information from Israeli soldiers by installing malicious programs on soldiers' smartphones that spy and record everything," he said.
A senior intelligence officer also stated in press remarks that over the past few months, dozens of soldiers and officers, mostly from combat units, were enticed into chatting with people they believed were young and attractive people in Israel and abroad.
He said that Hamas used Facebook as a medium to engage army personnel in conversations and encourage them to download a chat application to their cellphones.
The application, for both Android and iPhone, was used by Hamas to access vital data on phones, including contacts, personal text messages and photographs, and allowed its operatives to listen to conversations and take covert photos, the officer explained.
The intelligence officer also said he could not explain how those behind the hacking operation managed to hold conversations in perfect colloquial Hebrew, without making grammatical mistakes.
The army, however, refused to reveal any more details of the hack, including how it ascertained that Hamas was behind it.
Using fake profiles on social media with alluring photos, members of Hamas managed to network with soldiers and officers, luring them into long chats, Arabic-language spokesman for the Israeli army Avichay Adraee said in a Facebook post.
"Following reports from soldiers of suspicious activity of accounts on social media an operation was launched lasting several months led by the military intelligence aimed at uncovering enemy accounts," Adraee added
"During the operation, we uncovered dozens of accounts working to leak and steal information from Israeli soldiers by installing malicious programs on soldiers' smartphones that spy and record everything," he said.
A senior intelligence officer also stated in press remarks that over the past few months, dozens of soldiers and officers, mostly from combat units, were enticed into chatting with people they believed were young and attractive people in Israel and abroad.
He said that Hamas used Facebook as a medium to engage army personnel in conversations and encourage them to download a chat application to their cellphones.
The application, for both Android and iPhone, was used by Hamas to access vital data on phones, including contacts, personal text messages and photographs, and allowed its operatives to listen to conversations and take covert photos, the officer explained.
The intelligence officer also said he could not explain how those behind the hacking operation managed to hold conversations in perfect colloquial Hebrew, without making grammatical mistakes.
The army, however, refused to reveal any more details of the hack, including how it ascertained that Hamas was behind it.
11 jan 2017

Several of the women Hamas has imitated
Posing as attractive young women, Hamas operatives successfully managed to hack dozens of IDF soldiers' cell phones in an attempt to acquire intelligence on IDF forces near the Gaza border.
As part of the Hamas' internet espionage activities, the terrorist organization's cyber collections unit managed to hack dozens of cell phones belonging to IDF combat soldiers in an attempt to gather intelligence for military operations and preparations on the Gaza border.
As part of the Hamas' internet espionage activities, the terrorist organization's cyber collections unit managed to hack dozens of cell phones belonging to IDF combat soldiers in an attempt to gather intelligence for military operations and preparations on the Gaza border.
Hamas operatives would pose as attractive, young Israeli women by assuming their identities and making contact with soldiers, mainly through Facebook. Following contact with soldiers, the Hamas operatives would attempt to engage in an intimate virtual relationship and convince soldiers to download an "application" that would allow for video chatting.
The "application" was a Trojan horse, which gave Hamas total control over the device and allowed the terrorist organization to activate the camera and microphone, access contacts, videos and photos, and even Whatsapp conversations and emails—all without the soldier being aware.
Moreover, Hamas also managed to delete the application from the devices, while simultaneously installing more sophisticated monitoring and control applications without leaving a trace.
Posing as attractive young women, Hamas operatives successfully managed to hack dozens of IDF soldiers' cell phones in an attempt to acquire intelligence on IDF forces near the Gaza border.
As part of the Hamas' internet espionage activities, the terrorist organization's cyber collections unit managed to hack dozens of cell phones belonging to IDF combat soldiers in an attempt to gather intelligence for military operations and preparations on the Gaza border.
As part of the Hamas' internet espionage activities, the terrorist organization's cyber collections unit managed to hack dozens of cell phones belonging to IDF combat soldiers in an attempt to gather intelligence for military operations and preparations on the Gaza border.
Hamas operatives would pose as attractive, young Israeli women by assuming their identities and making contact with soldiers, mainly through Facebook. Following contact with soldiers, the Hamas operatives would attempt to engage in an intimate virtual relationship and convince soldiers to download an "application" that would allow for video chatting.
The "application" was a Trojan horse, which gave Hamas total control over the device and allowed the terrorist organization to activate the camera and microphone, access contacts, videos and photos, and even Whatsapp conversations and emails—all without the soldier being aware.
Moreover, Hamas also managed to delete the application from the devices, while simultaneously installing more sophisticated monitoring and control applications without leaving a trace.
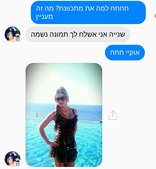
Chat transcript wherein Hamas operative attempts to entice soldier with a picture of "herself"
Dozens of soldiers whose cell phones were hacked were questioned by the IDF's Information Security Department and the affected devices were also confiscated in order to determine the extent of the damage.
Tests by the IDF and Shin Bet revealed that the damage was minimal, but acknowledged that Hamas acquired images that resembling IDF war rooms, tanks and armored vehicles, observation devices and locations of soldiers in the border area.
In response to the cyber attacks, the IDF has decided to release the images of 16 characters Hamas is using in the attempt to entice soldiers into giving up information.
At this time it is not known whether or not soldiers will face disciplinary action as a result of falling in a trap, but consultations with the Military Advocate General will make the final ruling on the matter.
Hamas members in reservists' groups on Facebook
Monitoring activities by the IDF's Information Security Department in 2016 uncovered Hamas attempts to enter open and closed Facebook groups of reserve soldiers who were attempting to keep in touch with their platoons and units.
Information gathered by the IDF demonstrates that Hamas built reliable profiles based on forged identities of soldiers. Posing as soldiers, Hamas operatives asked about recent training exercises and attempted to glean as much information as possible.
Following the increase of Hamas cyber activity, the IDF has decided to tighten guidelines for soldiers on the use of social media. From here on out, all soldiers in possession of a top secret security clearance will be forbidden from uploading any pictures related to military service or register as a soldier. Additionally, all officers above the rank of captain will also be required to abide by the same guidelines.
Given the impact of social media on the IDF in recent years, military officials have also decided to increase mandatory briefings and training on how to use social media as a soldier and the threat posed to security.
3,000 IDF-based Facebook groups
Dozens of soldiers whose cell phones were hacked were questioned by the IDF's Information Security Department and the affected devices were also confiscated in order to determine the extent of the damage.
Tests by the IDF and Shin Bet revealed that the damage was minimal, but acknowledged that Hamas acquired images that resembling IDF war rooms, tanks and armored vehicles, observation devices and locations of soldiers in the border area.
In response to the cyber attacks, the IDF has decided to release the images of 16 characters Hamas is using in the attempt to entice soldiers into giving up information.
At this time it is not known whether or not soldiers will face disciplinary action as a result of falling in a trap, but consultations with the Military Advocate General will make the final ruling on the matter.
Hamas members in reservists' groups on Facebook
Monitoring activities by the IDF's Information Security Department in 2016 uncovered Hamas attempts to enter open and closed Facebook groups of reserve soldiers who were attempting to keep in touch with their platoons and units.
Information gathered by the IDF demonstrates that Hamas built reliable profiles based on forged identities of soldiers. Posing as soldiers, Hamas operatives asked about recent training exercises and attempted to glean as much information as possible.
Following the increase of Hamas cyber activity, the IDF has decided to tighten guidelines for soldiers on the use of social media. From here on out, all soldiers in possession of a top secret security clearance will be forbidden from uploading any pictures related to military service or register as a soldier. Additionally, all officers above the rank of captain will also be required to abide by the same guidelines.
Given the impact of social media on the IDF in recent years, military officials have also decided to increase mandatory briefings and training on how to use social media as a soldier and the threat posed to security.
3,000 IDF-based Facebook groups

Despite the exposure of the Hamas operation, the IDF believes that the ongoing Hamas campaign will seek to employ more sophisticated means of gathering intelligence.
The IDF has also refused to comment on whether or not the situation on the northern border is worse due to the technological capabilities of Hezbollah, which utilizes both Iranian and Russian technology. However, the IDF has acknowledged that efforts against internet and cellular espionage are ongoing.
The IDF has identified 3,000 unofficial Facebook groups currently in operation. As a result, officials have decided that additional measures are necessary in order to avoid future lapses in security. Measures being discussed include more precautions such as permission to start groups and stricter guidelines for accepted friend requests.
As part of this operation, the IDF has opened a special command post available 24/7 where soldiers can report suspicious online activity.
Victims of the current cyber attack are identified mostly as low-ranking soldiers, with several officers included.
The IDF has also refused to comment on whether or not the situation on the northern border is worse due to the technological capabilities of Hezbollah, which utilizes both Iranian and Russian technology. However, the IDF has acknowledged that efforts against internet and cellular espionage are ongoing.
The IDF has identified 3,000 unofficial Facebook groups currently in operation. As a result, officials have decided that additional measures are necessary in order to avoid future lapses in security. Measures being discussed include more precautions such as permission to start groups and stricter guidelines for accepted friend requests.
As part of this operation, the IDF has opened a special command post available 24/7 where soldiers can report suspicious online activity.
Victims of the current cyber attack are identified mostly as low-ranking soldiers, with several officers included.
7 jan 2017

The Hamas Movement has strongly denounced Facebook for blocking dozens of Palestinian pages, describing the measure as “arbitrary” and “persistence in fulfilling Israel’s wishes.”
In a press release on Friday, Hamas spokesman Husam Badran said that the subscribers of these removed “pages have the right to express their points of view and to say what they have in mind.”
Badran urged Palestinian activists and news outlets to seriously look for effective alternatives to Facebook, stressing that this social networking site reached an advanced level in its antagonism towards the Palestinian people and their just cause.
The administration of Facebook on Friday launched a widespread suspension campaign against dozens of pages belonging to Hamas and Palestinian activists as part of its agreement with the Israeli regime to censure and remove anti-Israel accounts.
In a press release on Friday, Hamas spokesman Husam Badran said that the subscribers of these removed “pages have the right to express their points of view and to say what they have in mind.”
Badran urged Palestinian activists and news outlets to seriously look for effective alternatives to Facebook, stressing that this social networking site reached an advanced level in its antagonism towards the Palestinian people and their just cause.
The administration of Facebook on Friday launched a widespread suspension campaign against dozens of pages belonging to Hamas and Palestinian activists as part of its agreement with the Israeli regime to censure and remove anti-Israel accounts.

The administration of Facebook launched a widespread suspension campaign against dozens of pages linked to Hamas and Palestinian activists as part of its agreement with the Israeli regime to censure and remove anti-Israel accounts.
The campaign, which was described as the biggest compared to previous ones, targeted over 90 pages belonging to institutions, figures and activists believed to be affiliated with Hamas, in addition to 30 other accounts of individuals supporting the Palestinian people and their national cause.
This fierce Facebook campaign came close on the heels of the pro-Hamas campaign titled “Be like Ayyash,” which marked the 21th martyrdom anniversary of engineer Yahya Ayyash, a senior member of al-Qassam Brigades of Hamas and received widespread participation by social media users.
Facebook also blocked dozens of accounts belonging to Palestinian activists and citizens who joined and supported the social media campaign, “Be like Ayyash.
The campaign, which was described as the biggest compared to previous ones, targeted over 90 pages belonging to institutions, figures and activists believed to be affiliated with Hamas, in addition to 30 other accounts of individuals supporting the Palestinian people and their national cause.
This fierce Facebook campaign came close on the heels of the pro-Hamas campaign titled “Be like Ayyash,” which marked the 21th martyrdom anniversary of engineer Yahya Ayyash, a senior member of al-Qassam Brigades of Hamas and received widespread participation by social media users.
Facebook also blocked dozens of accounts belonging to Palestinian activists and citizens who joined and supported the social media campaign, “Be like Ayyash.
